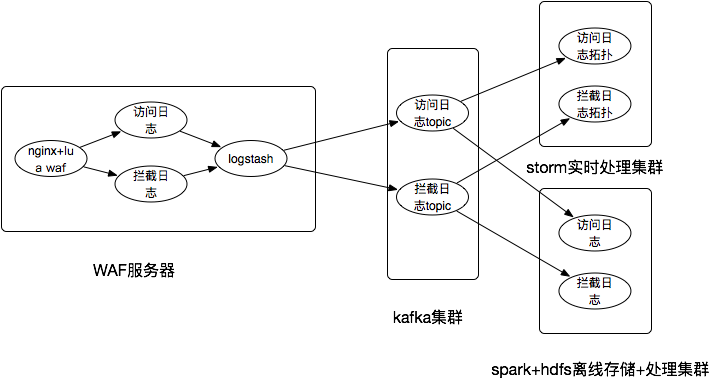
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
| use pscan;
SET FOREIGN_KEY_CHECKS=0;
-- ----------------------------
-- Table structure for waflog
-- ----------------------------
DROP TABLE IF EXISTS `waflog`;
CREATE TABLE `waflog` (
`id` int(100) NOT NULL,
`ip` varchar(100) DEFAULT NULL,
`website` varchar(255) DEFAULT NULL,
`time` datetime DEFAULT NULL,
`method` varchar(255) DEFAULT NULL,
`path` varchar(255) DEFAULT NULL,
`demo` varchar(255) DEFAULT NULL,
`agent` varchar(255) DEFAULT NULL,
`rule` varchar(255) DEFAULT NULL,
PRIMARY KEY (`id`)
) ENGINE=MyISAM DEFAULT CHARSET=utf8;
-- ----------------------------
-- Records of waflog
-- ----------------------------
INSERT INTO `waflog` VALUES ('1', '172.20.3.64', 'www.maliciouskr.cc', '2016-09-08 20:18:03', 'GET', '/dump.php?<img<!--+--> src=x onerror=alert(9549);//><!-- -->', '-', 'Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21', '(?:define|eval|file_get_contents|include|require|require_once|shell_exec|phpinfo|system|passthru|preg_\\w+|execute|echo|print|print_r|var_dump|(fp)open|alert|showmodaldialog)\\(\"');
INSERT INTO `waflog` VALUES ('2', '172.20.3.64', 'www.maliciouskr.cc', '2016-09-08 20:18:03', 'GET', '/dump.php?<img<!--+--> src=x onerror=alert(9549);//><!-- -->', '-', 'Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21', '(?:define|eval|file_get_contents|include|require|require_once|shell_exec|phpinfo|system|passthru|preg_\\w+|execute|echo|print|print_r|var_dump|(fp)open|alert|showmodaldialog)\\(\"');
INSERT INTO `waflog` VALUES ('3', '172.20.3.64', 'www.maliciouskr.cc', '2016-09-08 20:18:03', 'GET', '/dump.php?<img<!--+--> src=x onerror=alert(9549);//><!-- -->', '-', 'Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21', '(?:define|eval|file_get_contents|include|require|require_once|shell_exec|phpinfo|system|passthru|preg_\\w+|execute|echo|print|print_r|var_dump|(fp)open|alert|showmodaldialog)\\(\"');
INSERT INTO `waflog` VALUES ('4', '172.20.3.64', 'www.maliciouskr.cc', '2016-09-08 20:18:03', 'GET', '/dump.php?<img<!--+--> src=x onerror=alert(9549);//><!-- -->', '-', 'Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21', '(?:define|eval|file_get_contents|include|require|require_once|shell_exec|phpinfo|system|passthru|preg_\\w+|execute|echo|print|print_r|var_dump|(fp)open|alert|showmodaldialog)\\(\"');
INSERT INTO `waflog` VALUES ('5', '172.20.3.64', 'www.maliciouskr.cc', '2016-09-08 20:18:03', 'GET', '/dump.php?<img<!--+--> src=x onerror=alert(9549);//><!-- -->', '-', 'Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21', '(?:define|eval|file_get_contents|include|require|require_once|shell_exec|phpinfo|system|passthru|preg_\\w+|execute|echo|print|print_r|var_dump|(fp)open|alert|showmodaldialog)\\(\"');
INSERT INTO `waflog` VALUES ('6', '172.20.3.64', 'www.maliciouskr.cc', '2016-09-08 20:18:03', 'GET', '/dump.php?<img<!--+--> src=x onerror=alert(9549);//><!-- -->', '-', 'Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21', '(?:define|eval|file_get_contents|include|require|require_once|shell_exec|phpinfo|system|passthru|preg_\\w+|execute|echo|print|print_r|var_dump|(fp)open|alert|showmodaldialog)\\(\"');
INSERT INTO `waflog` VALUES ('7', '172.20.3.64', 'www.maliciouskr.cc', '2016-09-08 20:18:03', 'GET', '/dump.php?<img<!--+--> src=x onerror=alert(9549);//><!-- -->', '-', 'Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21', '(?:define|eval|file_get_contents|include|require|require_once|shell_exec|phpinfo|system|passthru|preg_\\w+|execute|echo|print|print_r|var_dump|(fp)open|alert|showmodaldialog)\\(\"');
INSERT INTO `waflog` VALUES ('8', '172.20.3.64', 'www.maliciouskr.cc', '2016-09-08 20:18:03', 'GET', '/dump.php?<img<!--+--> src=x onerror=alert(9549);//><!-- -->', '-', 'Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21', '(?:define|eval|file_get_contents|include|require|require_once|shell_exec|phpinfo|system|passthru|preg_\\w+|execute|echo|print|print_r|var_dump|(fp)open|alert|showmodaldialog)\\(\"');
INSERT INTO `waflog` VALUES ('9', '172.20.3.64', 'www.maliciouskr.cc', '2016-09-08 20:18:03', 'GET', '/dump.php?<img<!--+--> src=x onerror=alert(9549);//><!-- -->', '-', 'Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21', '(?:define|eval|file_get_contents|include|require|require_once|shell_exec|phpinfo|system|passthru|preg_\\w+|execute|echo|print|print_r|var_dump|(fp)open|alert|showmodaldialog)\\(\"');
|